Understanding SOC Audits in Cybersecurity
A practical guide to SOC 1, SOC 2, SOC 3 audits, report types, and standards, designed to enhance security evaluations and vendor trust.
In today’s cloud-driven business world, evaluating the security posture of service providers is critical. However, directly auditing every cloud vendor is impractical — which is where SOC audits come into play.
In this article, I explain the structure and purpose of SOC audits, with a focus on how different audit categories (SOC 1, SOC 2, SOC 3) and report types (Type 1, Type 2) impact both security assurance and compliance evaluations.
This piece demonstrates my ability to synthesize technical frameworks into clear, practical knowledge — an essential skill when designing secure systems, evaluating vendors, or advising organizations on risk management strategies.
SOC audits are rapidly growing in importance, especially in cybersecurity exams. They address a critical problem:
How can you trust that your cloud vendors are protecting your sensitive information?
You audit your own systems. But auditing every vendor yourself would be impossible — for both you and them.
SOC audits solve this.
Instead of sending teams to inspect vendors, companies rely on independent auditors. These auditors assess a vendor’s security controls and issue a report.
Vendors then share these reports with customers, offering confidence without the need for endless site visits.
Remember:
SOC = Service Organization Controls.
You don’t perform a SOC audit.
You receive the audit report from your service providers.
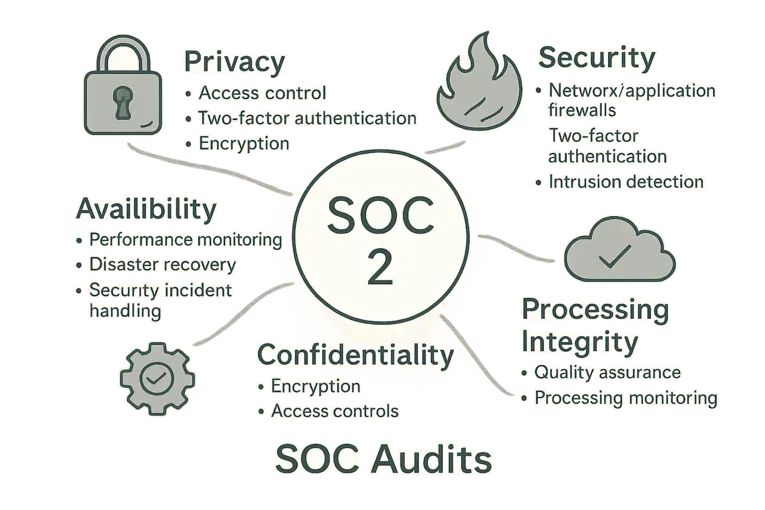
Categories of SOC Audits: SOC 1, SOC 2, SOC 3
SOC audits are divided into three categories, each with a specific focus:
| Category | Focus | Audience |
|---|---|---|
| SOC 1 | Financial reporting controls | For clients undergoing their own financial audits |
| SOC 2 | Confidentiality, integrity, availability, and privacy controls | For internal review under NDA |
| SOC 3 | Same security areas as SOC 2, but summarized | For public distribution |
Key Distinction:
- SOC 1 = Finance-focused.
- SOC 2/3 = Security and privacy-focused.
- SOC 2 = Private report.
- SOC 3 = Public report.
Types of SOC Reports: Type 1 vs. Type 2
Both SOC 1 and SOC 2 audits can produce two types of reports:
| Type | Meaning |
|---|---|
| Type 1 | Describes controls and evaluates their design suitability. Snapshot at a single point in time. |
| Type 2 | Describes controls plus the results of testing them over time (typically 6 months). |
Important:
SOC 3 reports don’t have Type 1 or Type 2.
They are always public and summarized.
Example:
- A SOC 2 Type 1 = Internal report about design only.
- A SOC 2 Type 2 = Internal report about design + operational effectiveness.
Standards Behind SOC Audits
Two standards govern how SOC audits are conducted:
| Standard | Jurisdiction |
|---|---|
| SSAE 18 | U.S. standard (AICPA) |
| ISAE 3402 | International standard (IAASB) |
Quick Tip:
SSAE 18 = US,
ISAE 3402 = International.
Quick Recap
- SOC 1 = Financial controls.
- SOC 2 = Confidentiality, integrity, availability, privacy.
- SOC 3 = Same controls as SOC 2, but public.
- Type 1 = Design assessment only.
- Type 2 = Design + operational testing.
- SSAE 18 = US standard, ISAE 3402 = International.
Closing Thoughts
Understanding SOC audits is more than passing certification exams — it’s about building informed trust in cloud ecosystems. Whether designing architectures, advising stakeholders, or reviewing vendor agreements, being able to quickly assess and communicate audit findings is a critical technical skill.
Thanks for reading!
Authored by Davi Luiz Guides
Part of the “Zero Trust Local Environment” series
Visit daviguides.github.io for more insights
